You never have enough of securing your machines, have you? As a developer, you are probably continuously striving the good balance between functionality and security of your platform. As a Cloud Developer, possibly on a well-known PaaS platform, you are relieved of most of the encumbrance, which is off-loaded to your provider, but still will need to deploy strategies to ensure that your app is as safe as possible for both you and your users. Well, nowadays we have plenty of resources to defend our website, especially on the cryptography side. Well, probably it’s not the right time to celebrate OpenSSL, the most common and used encryption layer around, but apart from bugs who might cause your heart to bleed (pun intended), the modern asymmetric cryptography technologies are quite robust and well-known, and upon them relies the vast majority of security of the Internet nowadays.
Nevertheless, cryptographers keep looking for ways to make things even more secure, and somehow new technology is slowly making its way to the tier-1 set of security algorithms: the Elliptic Curve Cryptography. Today’s news is: Microsoft added ECC to Azure Web Sites.
Wait, elliptic…what?
ECC is not the latest acronym in the computer world: mind immediately goes to Error Correcting Code RAM memory. When speaking about cryptography, though, ECC is an “approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields“, Wikipedia says. Quite easy, right?
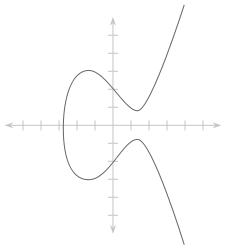

Let’s take it one bite a time. Mathematically speaking, Elliptic curves are based on equations like “y^2 = x^3 + ax + b”. Once drawn, they produce graphs like this one on the left here. As you might see, the curve has a peculiar elliptic shape and is symmetric. A long and deep (and boring, probably) analysis of the mathematical properties of this kind of curves should be here, but long story short: elliptic curves have a number of interesting features that we can use to derive public keys from private ones very easily, while the other way round is extremely more complex, by at least one order of magnitude. For example, a reasonably strong 3072 bit RSA key is equivalent to a small 256 bit ECC key. Quite impressive, I’d daresay.
ECC in Azure Web Sites
To unleash all the computational efficiency of ECC cryptography in Azure Web Sites is quite easy thanks to the new feature Microsoft added. The starting point is buying an ECC certificate instead of an ordinary SSL one. ECC is quite a new technology out there, so you might find a little bit difficult to provide one for yourself. Right now, Symantec and Entrust sell them, but you can expect more companies will join the band soon. Once you have it, enough you upload it to Azure as a PFX file, just like for your usual RSA certificate, and assign it to your site, and you’re done. Azure will take care of everything it’s needed in the background to make it up and running. Anyway, caution ahead: ECC is not yet supported by all the clients around. The most recent ones support this new toy in a good way but ensure to provide a backup for the older ones, just in case.



