In on-premises environments, data security is typically a siloed activity, with a company’s security team telling the internal technology groups (server administration, database, networking, and so on) what needs to be protected against intrusion.
This approach is absolutely a bad idea for cloud platforms such as Microsoft Azure. Security is everyone’s job and should be one of the key elements of every cloud solution design. It’s vital that everyone involved is aware of the best practices and platform capabilities.
Fortunately, there are an abundance of tools, methods, and information available to help with securely deploying cloud applications and the virtual networks supporting them. In this post, we’ll take a brief tour of Azure’s encryption techniques, its usage, and the available customizations focused on three important areas:
- How Azure Encrypts Data at Rest
- How Azure Encrypts Data in Flight
- Azure Key Management
Azure Encryption of Data at Rest
Encryption of data at rest protects stored information from unwanted access. For example, at-rest encryption could protect the contents of your hard drive if it were lost or stolen.
This is a high-level overview of the encryption workflow for data written to and retrieved from Azure Blob storage:


By default, data written to Azure Blob storage is encrypted when placed on disk and decrypted when accessed using Azure Storage Service Encryption, Azure Key Vault, and Azure Active Directory (which provide secure, centrally managed key management and role-based access control, or RBAC).
Azure also provides encryption for data at rest for files stored in its database platforms such as Azure SQL. Using transparent data encryption, the contents of a database can be encrypted and decrypted through the use of symmetric keys (essentially, a shared secret) managed by Azure Key Vault (encryption at rest is the default for Azure Cosmos DB):


Virtual machines aren’t left out of Azure’s data-at-rest encryption capabilities if you use managed disks (Azure Key Vault managed encryption is enabled by default on managed disks). Check out the managed disk FAQ for more detailed information.
Azure Encryption of Data In-flight
Data in flight (for example, data transfers over the open internet to cloud storage, web sessions and other types of data movement) must be protected against eavesdropping, interception, and tampering. All sessions with Azure services and data centers are secured using the Transport Layer Security (TLS) cryptographic protocol and Forward Secrecy (also known as Perfect Forward Secrecy or PFS), a key agreement protocol:


The TLS Wikipedia article summarizes its critical features:
– The [TLS encrypted] connection is private (or secure) because symmetric cryptography is used to encrypt the data transmitted. The keys for this symmetric encryption are generated uniquely for each connection and are based on a shared secret negotiated at the start of the session
– The identity of the communicating parties can be authenticated using public-key cryptography.
– The connection is reliable because each message transmitted includes a message integrity check using a message authentication code to prevent undetected loss or alteration of the data during transmission.
Perfect Forward Secrecy (PFS) is a fascinating methodology used by Microsoft to further ensure the security of communication with cloud services. Turning again to the Wikipedia article on PFS, it
“…is a feature of specific key agreement protocols that gives assurances your session keys will not be compromised even if the private key of the server is compromised. Forward secrecy protects past sessions against future compromises of secret keys or passwords. By generating a unique session key for every session a user initiates, even the compromise of a single session key will not affect any data other than that exchanged in the specific session protected by that particular key.”
Secure Communication with Azure Virtual Networks Using VPN
Azure supports the creation of encrypted Virtual Private Network (VPN) tunnels with Azure virtual networks. The two available methods are point to site VPN, which connects an individual client machine to a virtual network and site to site VPN which connects a site to Azure using an on-premises VPN device connected to an Azure VPN Gateway:
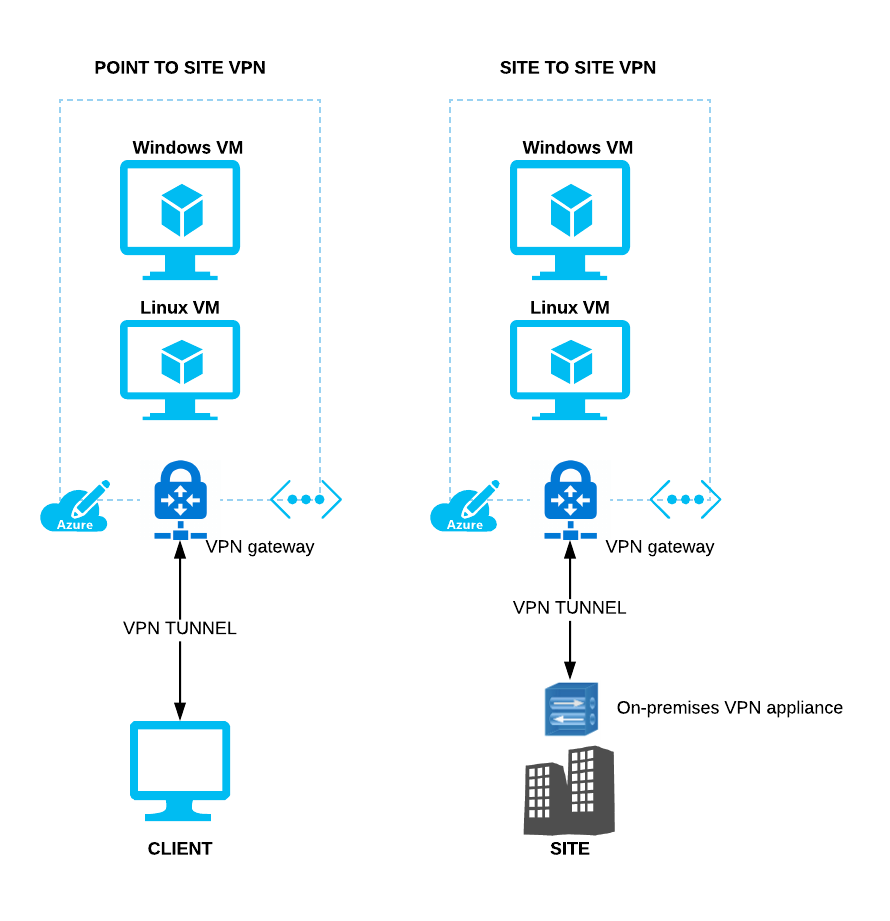

Secure Communication with Azure Virtual Machines
When securely communicating with virtual machines in Azure virtual networks, you use two methods:
- Remote Desktop Protocol (Windows and Linux VMs, protected by TLS)
- Secure Shell – SSH – (Linux VMs, protected by public/private key pair, asymmetric encryption)


By now you’ve probably noticed the repeated mention of Azure Key Vault as the recommended, central source for key storage, generation, logging, and management. Microsoft describes the Key Vault offering:
“Azure Key Vault helps safeguard cryptographic keys and secrets used by cloud applications and services. By using Key Vault, you can encrypt keys and secrets (such as authentication keys, storage account keys, data encryption keys, .PFX files, and passwords) using keys protected by hardware security modules (HSMs). For added assurance, you can import or generate keys in HSMs. If you choose to do this, Microsoft processes your keys in FIPS 140-2 Level 2 validated HSMs (hardware and firmware).”
The graphic below illustrates the benefits and use cases of Azure Key Vault:


Azure Key Vault provides you with a platform-native, feature-rich toolkit for deploying, storing, and tracking usage of the keys you’ll use to secure the applications you build. Although experienced enterprise IT organizations moving to Azure may be tempted to build their own systems for key management (duplicating what’s been done on-premises), Key Vault should always be considered first as the preferred solution.
Well, that brings our brief tour of Azure’s encryption techniques to an end. For more information, and to get started using Azure Key Vault, check out the following resources:
- Azure security overview
- Azure network security overview
- Azure database security overview
- Azure virtual machines security overview
- Data encryption at rest
- Data security and encryption best practices
I also recommend the following content from Cloud Academy to learn how to work with and apply Azure Key Vault for your deployments:
- Hands-on Lab: Azure Key Vault and Disk Encryption: Work in the Azure console to use the Azure Key Vault service to store keys and secrets used to encrypt an Azure Virtual Machine.
- Learning Path: Azure Services for Security Engineers: Apply Key Vault and other Azure security features and services to enable strong security practices and to protect and secure your own cloud applications.
Happy learning and good luck on your cloud journey!



