Overview of Google Cloud IAM: Roles, Best Practices, and Conditions

Google Cloud Identity and Access Management (IAM) allows users to access specific cloud resources while preventing unauthorized access to any resource in Google Cloud Platform (GCP). One of the main security tenets of cloud services in general, which states that no one should be granted additional permissions without the principal user’s consent, is a good analogy to the function performed by GCP IAM. To preserve the integrity and data security of the businesses’ technology environments, which are expanding to include several Google cloud resources, authorized access must be made available, but only to the right users and in a “least privilege” manner.
GCP Identity and Access Management has a stellar reputation for its security capabilities. The small to medium and large enterprises who are adapting Google Cloud Platform for cloud services and its resources should have a clear understanding of how to best leverage Google Cloud IAM, since understanding this function or service will help those businesses ensure the security of their workload and resources in the future.
With Google Cloud Identity and Access Management, you have the power to limit who has access to particular resources by defining who (identity) is willing to access what (role) for a specific resource in Google Cloud infrastructure. It entails that you will be specifying the identification of everyone who will have access to or authority over a certain cloud resource. Google offers a variety of cloud resources, including GKE Clusters, Compute Engine VM (virtual machine) instances, and more. Not only may you limit access to them, but also to the projects you are working on and the folders that contain vital information about your resources.
As we described in the previous section Google Cloud IAM is responsible to define who (identity) is willing to access what (role) for which cloud resource. Some examples of resources can be: instances of VMs running on Compute Engine, clusters of Google Kubernetes Engine (GKE), and buckets of Cloud Storage. Resources include the projects, folders, and associations you use to arrange your resources.
In Google Cloud IAM, the end user isn’t permitted to access a resource directly. Instead, GCP IAM roles are used to organize permissions, and authorized principals are given access to roles. Note: Principals were frequently referred to as members by Google Cloud IAM in the past and this name is still used by some APIs.
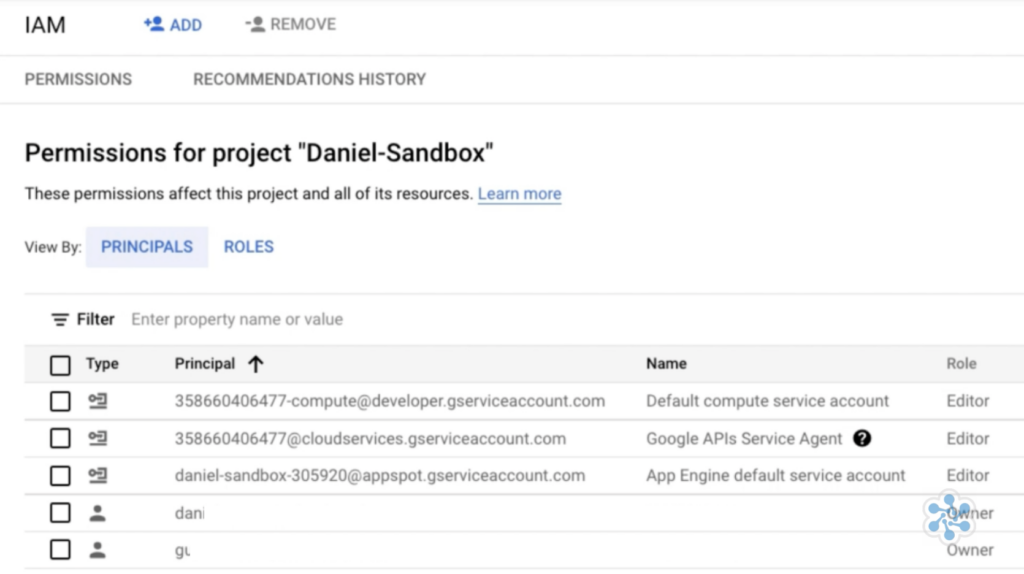

The roles assigned to principals are specified and enforced by an allow policy, also known as a Google IAM policy. A resource is associated with each allowed policy and GCP IAM evaluates the resource’s allow policy when an authenticated principal tries to access it to see if the action is allowed.
The components of GCP IAM hold the collection of permissions in the roles that need to be monitored. However, before doing that, you need to be familiar with the various Google Cloud IAM role types that are:
The fundamental Google IAM roles are editor, viewer, and owner. Before consumers were made aware of GCP IAM, these roles were in use. Since all of these jobs are interdependent on one another, the Editor position’s permissions make up the Owner role. Additionally, the Viewer role’s permissions make up the Editor role. The Cloud Console, the GCP tool, or Google Cloud API can all be used to apply the basic roles to a service or project.
Granular access to the particular services that Google Cloud manages is provided via predefined roles. It permits access to the Google Cloud resources while taking steps to restrict unauthorized access to all other resources. Google keeps track of predefined roles and takes the necessary steps to update permissions. Typically, it occurs whenever Google introduces new products or services.
This particular job lets you provide users granular access to the user-specific permission list. In addition to established roles, Google Cloud IAM gives users the freedom to create their own IAM custom roles. You may add a single or many particular permissions to GCP IAM custom roles. You can establish and maintain the custom roles and then allocate them to the users who are crucial to your company.
A service account is a unique type of account that is utilized by a VM instance or an application rather than a user. Using service accounts in Google Cloud infrastructure, workloads create allowable Google Cloud API calls which can be either: Google Workspace, Google Identity users via domain-based delegation, or the service account itself.
A service account can be specified as service-account-name@project-id.iam.gserviceaccount.com. Each service account uses two sets of private/public RSA (Rivest, Shamir, Adleman) key pairs for Google authentication.
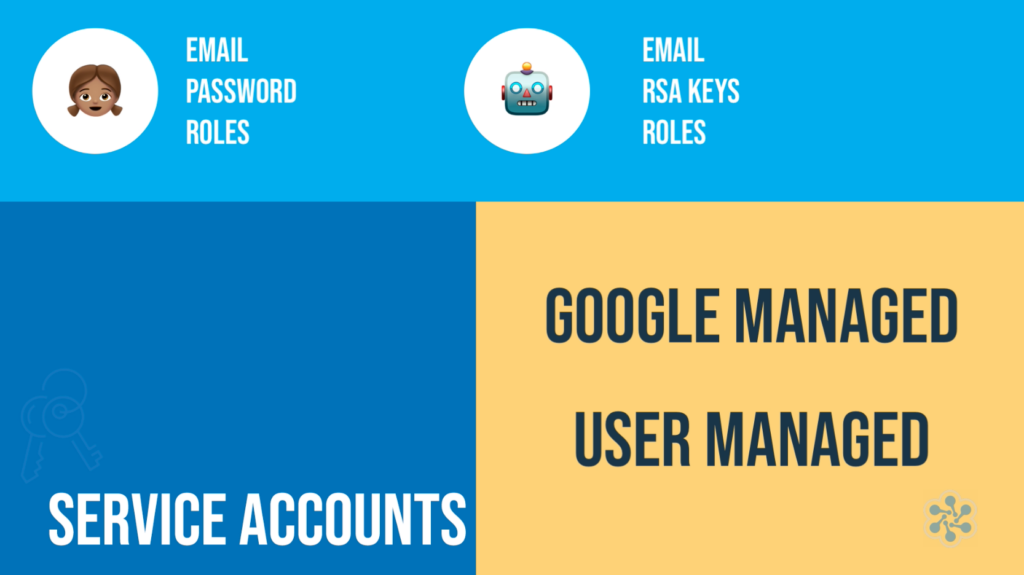

There are three prominent service account categories:
User-managed: Service accounts created and controlled by GCP project administrators.
Default: The administrator of a project may control service accounts that Google creates. They are recommended to be associated with a resource of a certain type as the default service account. The Compute Engine Default Service Account, for example, which by default has the “Editor” basic role on a project submitted to it, illustrates how these default service accounts occasionally have access that is quite permissive and why understanding how these methods operate is crucial.
Google-managed: Google-managed service accounts are granted specific roles by default and these accounts are created when relevant services need to access Google cloud resources in a specific project. This account can be removed by a project administrator at any time.
The following are some recommendations for Google IAM best practices:
For Google Cloud resources, conditional, attribute-based access control can be specified and implemented using GCP IAM Conditions.
You can decide to only grant access to principals using Google Cloud IAM Conditions if certain requirements are satisfied. For instance, you may give users temporary access so they can fix a production problem, or you could only grant access to staff members who request it from your corporate office.
The allow policy of a resource’s role bindings specifies conditions. When a condition is present, access is only granted if the expression that makes up the condition evaluates to true. Each condition expression’s logic statements list one or more properties to be checked.
Google Cloud IAM Conditions cannot be applied when allocating basic roles like the Editor job or the Owner role (roles/editor). Additionally, you are unable to apply Google IAM conditions when granting roles to all users or all users who have authenticated.
As a part of permitted policies, role bindings have the following structure:
"bindings": [
{
"position": ...,
"components": ...,
"state": ...
},
...
]There may be 0 or 1 condition per role binding; the condition object is optional. In the absence of a condition object in a role binding, the principals always have the designated role on the resource.
Role bindings with GCP IAM conditions do not take precedence over those without conditions. When a principal is assigned a role and the role binding is not subject to a condition, the principal always occupies the assigned role. No matter if the principle is included in a constrained binding for the same role, the binding remains conditional.
The condition object’s structure is as follows:
"state/condition": {
"title": ...,
"description": ...,
"expression": ...
}The description of the ailment is not necessary, but its title is. The sole purpose of the title and description fields is to aid in identifying and describing the illness.
After utilizing a portion of Common Expression Language (CEL), an attribute-based logic expression is defined. Multiple statements may be used in the condition expression; each statement evaluates a different characteristic. The CEL language standard specifies that statements are combined using logical operators.
Gcloud IAM enables you to restrict access to other resources and allows you to offer granular access to particular Google Cloud resources. You may adhere to the security concept of least privilege using IAM, which states no one should be granted further permissions than they require.
Cloud administrators and developers have a foundation for building an effective and secure developer infrastructure thanks to the delegation of Google Cloud IAM roles across an enterprise. Setting up a secure hierarchy across projects and organizations by segmenting responsibilities into basic, predefined, and custom categories and outlining each category’s restrictions can be quite effective.

