Amazon security requires the use of AWS IAM with temporary authentication credentials. We’ll explore implementation via the command line and SDKs.
Cloud security is shared between AWS and its customers. Amazon Web Services Security takes responsibility for the compute and networking layers (security of the cloud), while we’re on the hook for our instances, networks, web applications, and databases (security in the cloud). But, as I discussed in a previous post on AWS security, Amazon also provides you with powerful tools to help you maintain your side of the deal; especially their Identity and Access Management system (IAM).
IAM allows you to create and manage permissions for multiple users. It works on the philosophy of least privilege, by providing only the precise rights a user or role will need to do exactly their task and nothing more. AWS best practices are, as the name suggests, the very best way to tighten your AWS IAM security. While most best practices can be implemented without modification, using IAM roles for apps or scripts running on EC2 instances might require a little work. In this post, we’ll see some examples of code-based IAM role implementation in your applications.
What is an AWS IAM role and how does it work
When AWS IAM users want to access the AWS Management Console, they log in using their usernames and passwords. Programmatic access to AWS services requires an Access Key and Secret Key. Your keys might look something like this (use this guide to create your own keys):
aws_access_key_id = ARTDOSFODNN7EXAMPLE aws_secret_access_key = wJalrXUtnTRSMI/K756ENG/bPxRfiCYEXAMPLEKEY
You could hard code your access keys in your application to enable access to AWS services like S3 or DynamoDB, but anyone with access to the code will be able to see the keys in plain text. If your server gets hacked, imagine the consequences of having left code like this lying around:
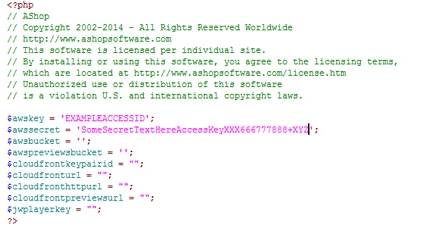

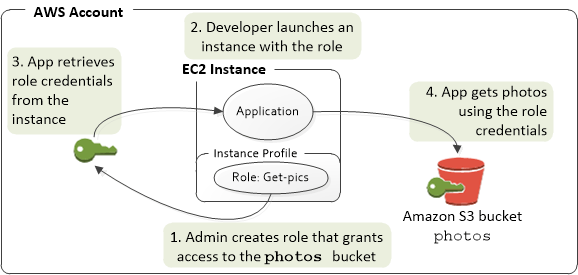

Benefits:
- No need to share permanent security credentials.
- Uses temporary security credentials when making requests from running EC2 instance. Effective Amazon security requires the use of AWS IAM with temporary authentication credentials: we’ll explore implementation via the command line and SDKs to AWS services.
- Integrated with All AWS Software Development Kits (SDKs) and the command line interface tool (CLI).
Creating an AWS IAM role
- Log into the IAM console.
- Click on Roles on the left panel, and then click Create New Role.
- Specify a descriptive Role name.

- Select Role Type as EC2.

- On the Attach Policy page, you can either select an existing policy or go back and create a new policy as per your needs.
- Review the role information, and then click Create Role.
- You can launch an instance using either a CLI or the Console: in Ec2 dashboard, click Launch Instance.
- Select your AMI, then select an instance type and click Next: Configure Instance Details.
- On the Configure Instance Details page, Specify the role when you launch your instances.

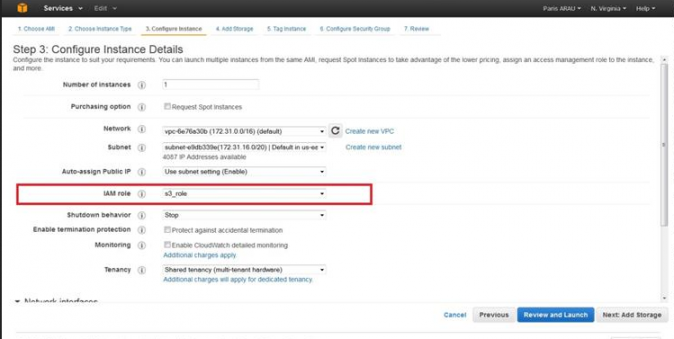
- Once this is done, your application will retrieve a set of temporary credentials and use them in your application.
Using AWS IAM Roles with the command line interface
Here’s a simple script to launch an instance using the AWS CLI. As you can see for yourself, we have included no AWS Keys. The “/etc/profile.d/aws-apitools-common.sh” file provides all the authentication you’ll need at run time (note, that if you’re running an AMI besides Amazon Linux, you may need to install this file manually).
#!/bin/bash . /etc/profile.d/aws-apitools-common.sh aws ec2 run-instances --image-id ami-1ecae776 --region us-east-1 --placement AvailabilityZone=us-east-1b --instance-type t2.large --key-name demo-key --subnet-id subnet-45874145 --security-group-ids sg-1254854
Using AWS IAM Roles with the PHP SDK
When using an IAM role with a PHP application, you can create caching layers on top of your IAM role credentials to specify a credentials cache using the credentials.cache option in a client’s factory method, or in a service builder configuration file. The configuration setting (credentials.cache) should be configured to an object that implements Guzzle’s CacheAdapterInterface . A credential’s cache can also be used in a service builder configuration.
<?php
// File saved as /path/to/custom/config.php
use Doctrine\Common\Cache\FilesystemCache;
use Guzzle\Cache\DoctrineCacheAdapter;
$cacheAdapter = new DoctrineCacheAdapter(new FilesystemCache('/tmp/cache'));
return array(
'includes' => array('_aws'),
'services' => array(
'default_settings' => array(
'params' => array(
'credentials.cache' => $cacheAdapter
)
)
)
);
Using AWS IAM Roles with the Java SDK
In order to use the AWS java SDK to connect AWS IAM service, all dependent Packages related to AWS IAM and AWS credentials need to be specified in the build path. The Java SDK uses “Class InstanceProfileCredentialsProvider” that loads credentials from the Amazon EC2 Instance Metadata Service, which retrieves temporary AWS credentials that have the same permissions as the IAM role associated with our EC2 instance. At the start of your program, you need to import the “com.amazonaws.auth.*” class.
import com.amazonaws.auth.profile.ProfileCredentialsProvider;
Using AWS IAM Roles with the Ruby SDK
In the Ruby SDK, EC2Provider objects retrieve credentials with the same permissions as the IAM role. These credentials refresh regularly to get access to AWS services.
AWS.config(:credential_provider => AWS::Core::CredentialProviders::EC2Provider.new)
Here’s a sample program that will download an object from AWS S3. As you can see, we have used no credentials within the code.
require 'rubygems'
require 'aws-sdk'
s3 = AWS::S3.newaws-iam-instance
bucket_name = 'text-content'
obj_name = 'text-object.txt'
document = s3.buckets[bucket_name].objects[obj_name]
File.open(obj_name, "w") do |f|
f.write(document.read)
end
puts "'#{obj_name}' copied from S3."



