Being able to easily access your cloud instances from the Public Internet is one of the most requested features from developers and system administrators. If you deploy your instances either in EC2-Classic or EC2-VPC public subnet, you can reach the machines easily by opening the 22 port to the public. But is this a safe way to connect to your servers? NO, not really.
Usually, DevOps and sysadmins create a Bastion host in order to access any other cloud instance from the Public Internet. In this case, you will open the 22 port to the public on the Bastion host Security Group and for the rest of the machines, you can open the 22 port only for the Bastion host Security Group. In this way you can easily add a hop in your connection process: only Bastion Hosts have access to your cloud instances inside AWS.
Even if a Bastion Host could be the first solution, this is not we are looking for when we are dealing with security in the cloud. In fact, you can easily get your Bastion host compromised by hackers and they would get access to all the machines behind this “firewall”.
Multi-Factor Authentication (MFA) is the solution we are looking for. Along with user username and password, users should enter the dynamically generated MFA code to login into cloud instances.
To set up the MFA, Google has an open source tool called Google Authenticator, which is widely covered on all the platforms for Multi-Factor Authentication (MFA) or Two-Factor Authentication (TFA).
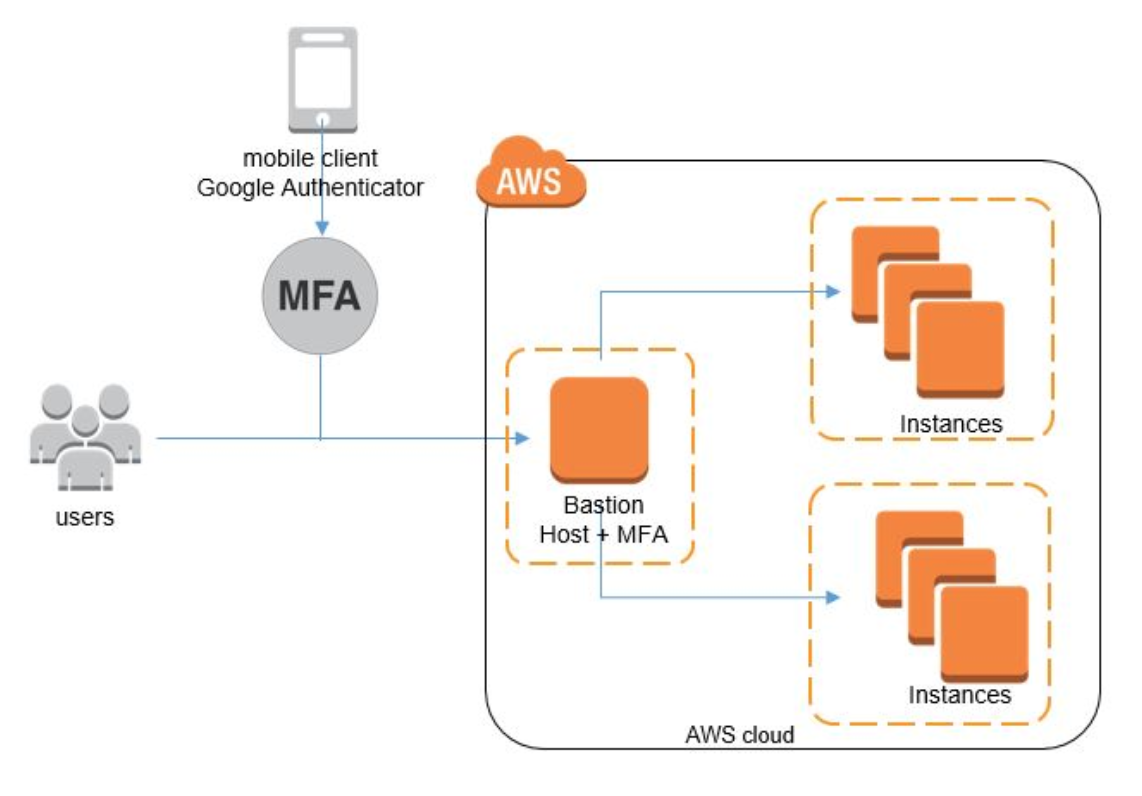

Let me show you how to set up the MFA authentication on a Linux machine.
Setup the Google Authenticator on Linux Bastion host
To enable the MFA on the Linux Bastion host, we need to set up the Google Authenticator PAM module for the machine that you want to enable with MFA.
- . Linux uses PAM (Pluggable Authentication Module) to integrate the Google Authenticator MFA. So make sure that PAM and PAM-Devel packages are installed on your system. If not, please install them.
# yum install pam.x86_64
# yum install pam-devel.x86_64 - Download the latest stable release Google Authenticator source package
# wget https://google-authenticator.googlecode.com/files/libpam-google-authenticator-1.0-source.tar.bz2 - Unzip the package and navigate to the package directory
# bunzip2 libpam-google-authenticator-1.0-source.tar.bz2
# tar -xf libpam-google-authenticator-1.0-source.tar
# cd libpam-google-authenticator-1.0 - Install the package into the system
#make
#make install - Make changes to the PAM and SSH configuration files to enable the Multi-Factor Authentication over SSH logins.
auth required pam_google_authenticator.so – Add this to the /etc/pam.d/sshd
In /etc/ssh/sshd_config, change the two parameters to yes and save it
PasswordAuthentication yes
ChallengeResponseAuthentication yes
Restart the sshd service – # /etc/init.d/sshd restart - Switch to the user to whom you want to enable the MFA and run the google-authenticator command. This will generate the new secret key and distribute it to the respective user
In this example, I have used mfauser
# su – mfauser
#google-authenticator
Setup the Google Authenticator App in Mobile Phone
Now, we need to set up the Google Authenticator App in our mobile device. You can find the Google Authenticator app in all the major mobile platforms like Android, iOS and Windows Phone.
Here are the steps to install and configure the Google Authenticator
- Install the Google Authenticator from the vendor App Store. It is freely available in all the top platforms (Android, iOS and Windows Phone). In this example, I used the Windows Phone app.
The app is available for Windows Operating system users also: https://code.google.com/p/gauth4win - Open the app and click on “+” button to add the name of the account and secret key
- Provide the Account name of your convenient and enter the secret key received from your administrator and click on “save” button
It would be good, if you give the Account name as : username@machinehostname - Now, you can see the new account added in your Authenticator dashboard.
Logging into the Linux server along with MFA
- Use SSH client to connect to the Linux server remotely using Linux/Mac native SSH client or putty from Windows
ssh mfauser@bastionhost - It will prompt for both Verification code and Password. Enter the 6-digit dynamically generated number from your mobile Google Authenticator app of this account as a verification code and then your standard password. Please enter the 6-digit number before it expires, otherwise, it will generate a new number and again you have to go through entering the password and then a new Verification code.
We are done. Your server access is now protected by MFA.
Important note: The Multi-Factor authentication works with the only password based SSH login. If you are using any private/public key SSH session, it will ignore MFA and log you indirectly. So please disable the ssh key based authentication on SSH configuration of your server.



