Let’s discuss VPC Endpoint’s value, common use cases, and how to get it up and running with the AWS CLI.
Last month Amazon Web Services introduced VPC Endpoint for Amazon S3. In this article, I am going to explain exactly what this means, how it will change – and improve – the way AWS resources communicate with each other, and how you can get it running with the AWS CLI.
Not that it’s quite complete yet, mind you:
Currently, we support endpoints for connections with Amazon S3 within the same region only. We’ll add support for other AWS services later.
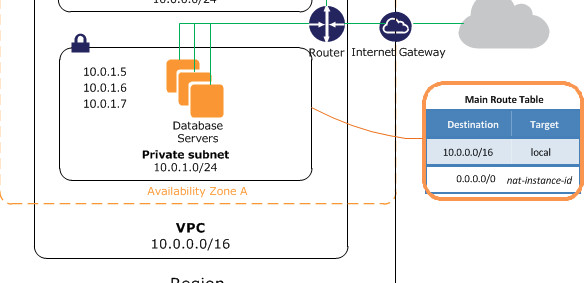
Accessing S3 the old way (without VPC Endpoint)
Traditionally, when creating a VPC with a private subnet you would set up security groups and access control lists (ACLs) to control inbound and outbound traffic. Because this is a private subnet, by default it has no access to any outside public resources. Consequently, should you need access to an outside resource, you would need to set up an Internet Gateway and route traffic through a NAT instance.
So, for example, if your EC2 instance runs an application that needs access to a file stored in an S3 bucket, before VPC Endpoint, this illustrates the only way it could be done:

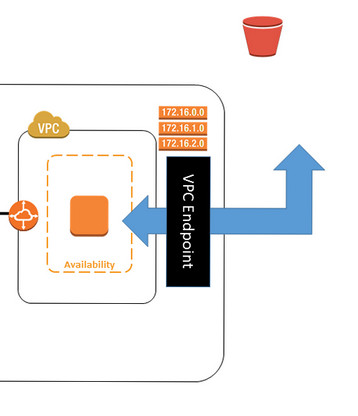
Accessing S3 with VPC Endpoint
Now, however, accessing S3 resources from within a private VPC subnet is much simpler. There’s no longer any need to configure a gateway or NAT instances. And as an added bonus, these endpoints are easy to set up, highly reliable, and provide a secure connection to S3.

If you’d prefer to work with the console to create a VPC Endpoint, you can easily follow the clear directions from the official AWS Blog. However, I am going to show you how to do it using the AWS CLI. (By the way, Cloud Academy has a great course guiding you through the AWS CLI if you could use some help).
Creating and Using VPC Endpoints with the AWS CLI
When we create our VPC endpoint we will use the following commands
- describe-route-tables (Get our VPC Id and route table for the endpoint)
- create-vpc-endpoint (Create your VPC endpoint)
- describe-vpc-endpoints (List your VPC endpoint)
- delete-vpc-endpoints (Delete a VPC endpoint)
So first, get our VPC ID and route table ID to use for the endpoint
$ aws ec2 describe-route-tables
Your output should look something like this:
-------------------------------------------------------------------------------------------------------- | DescribeRouteTables | +------------------------------------------------------------------------------------------------------+ || RouteTables || |+-------------------------------------------------+--------------------------------------------------+| || RouteTableId | rtb-0404a561 || || VpcId | vpc-731e0711 || |+-------------------------------------------------+--------------------------------------------------+| ||| Associations ||| ||+------------------------------------------------------+-------------------------------------------+|| ||| Main | False ||| ||| RouteTableAssociationId | rtbassoc-a4339dc1 ||| ||| RouteTableId | rtb-0404a561 ||| ||| SubnetId | subnet-fcbb5b99 ||| ||+------------------------------------------------------+-------------------------------------------+|| ||| Routes ||| ||+-----------------------------------------------------+--------------------------------------------+|| ||| DestinationCidrBlock | 172.31.0.0/16 ||| ||| GatewayId | local ||| ||| Origin | CreateRouteTable ||| ||| State | active ||| ||+-----------------------------------------------------+--------------------------------------------+|| ||| Tags ||| ||+---------------------------------+----------------------------------------------------------------+|| ||| Key | Name ||| ||| Value | endpointroute ||| ||+---------------------------------+----------------------------------------------------------------+|| || RouteTables || |+-------------------------------------------------+--------------------------------------------------+| || RouteTableId | rtb-b1849cd3 || || VpcId | vpc-731e0711 || |+-------------------------------------------------+--------------------------------------------------+| ||| Associations ||| ||+------------------------------------------------------+-------------------------------------------+|| ||| Main | True ||| ||| RouteTableAssociationId | rtbassoc-9f0f14fd ||| ||| RouteTableId | rtb-b1849cd3 ||| ||+------------------------------------------------------+-------------------------------------------+|| ||| Routes ||| ||+----------------------+---------------------------+----------------+-------------------+----------+|| ||| DestinationCidrBlock | DestinationPrefixListId | GatewayId | Origin | State ||| ||+----------------------+---------------------------+----------------+-------------------+----------+|| ||| 172.31.0.0/16 | | local | CreateRouteTable | active ||| ||| 0.0.0.0/0 | | igw-1b312779 | CreateRoute | active ||| ||| | pl-6ca54005 | vpce-d7b652be | CreateRoute | active ||| ||+----------------------+---------------------------+----------------+-------------------+----------+||
This tells me that my VPC ID is vpc-731e0711, and my Route Table Id (the one connected to a subnet) is rtb-0404a561.
Now let’s create a VPC endpoint. Remember that AWS currently supports endpoints within a single region, so we should note that my default region is ap-southeast-2.
$ aws ec2 create-vpc-endpoint --vpc-id vpc-731e0711 --service-name com.amazonaws.ap-southeast-2.s3 --route-table-ids rtb-0404a561
Here’s my output:
-------------------------------------------------------------------------------------------------------------------------------------------
| CreateVpcEndpoint |
+-----------------------------------------------------------------------------------------------------------------------------------------+
|| VpcEndpoint ||
|+-------------------+-------------------------------------------------------------------------------------------------------------------+|
|| CreationTimestamp| 2015-06-04T02:45:52Z ||
|| PolicyDocument | {"Version":"2008-10-17","Statement":[{"Sid":"","Effect":"Allow","Principal":"*","Action":"*","Resource":"*"}]} ||
|| ServiceName | com.amazonaws.ap-southeast-2.s3 ||
|| State | available ||
|| VpcEndpointId | vpce-97b652fe ||
|| VpcId | vpc-731e0711 ||
|+-------------------+-------------------------------------------------------------------------------------------------------------------+|
||| RouteTableIds |||
||+-------------------------------------------------------------------------------------------------------------------------------------+||
||| rtb-0404a561 |||
||+-------------------------------------------------------------------------------------------------------------------------------------+||
You should now have a VpcEndpoint connecting your VPC to an Amazon S3 service in the region you chose. You can now list your VpcEndpoint and the output should be similar to what you got above – unless you created more than one VpcEndpoint:
$ aws ec2 describe-vpc-endpoints
Finally, if you don’t plan on using this again, you can delete the VpcEndpoint using the following:
$ aws ec2 delete-vpc-endpoints --vpc-endpoint-ids vpce-97b652fe
What does all this now mean?
Even once you create a VPC Endpoint, the S3 public endpoints and DNS names will continue to work as they always have. All that the EndPoint does is add a new way by which the requests are routed from your private subnet to S3. Remember also that endpoints are virtual devices: they are horizontally scaled, redundant, and highly available VPC components that allow low-risk communication between instances in your VPC and AWS services.
What an endpoint effectively does is enable instances in your VPC to use their private IP addresses to communicate with resources in other services. Consequently, your instances do not require public IP addresses, and you do not need an Internet Gateway, a NAT instance, or a virtual private gateway in your VPC. This is because you use endpoint policies to control access to resources in other services. Traffic between your VPC and the AWS service does not leave the Amazon network.
Best of all, there is no additional charge for using endpoints. You will, of course, be charged standard charges for data transfer and resource use.



