Moving data to the cloud is one of the cornerstones of any cloud migration. Apache NiFi is an open source tool that enables you to easily move and process data using a graphical user interface (GUI). In this blog post, we will examine a simple way to move data to the cloud using NiFi complete with practical steps. Calculated Systems offers a cloud-first version of NiFi that you can use to follow along.
Cloud Object Storage
There are many ways to store data on the cloud, but the easiest are the object stores. All three major cloud providers have them:
These is an ideal starting point for files as you can typically land the files without too much forethought or capacity planning. Additionally, these object stores are extremely robust, featuring multiple levels of durability and availability.


For the purposes of this tutorial, we will start with the most common object store: Amazon Simple Storage Service (Amazon S3).
Amazon S3 Terminology
Before we get started moving data, let’s establish some basic terminology:
-
Identity and Access Management (IAM) – Controls for making and controlling who and what can interact with your AWS resources.
-
Access Keys – These are your access credentials to use AWS. These are not your typical username/password — they are generated using access identity management.
-
Bucket – A grouping of similar files that must have a unique name. These can be made publicly accessible and are often used to host static objects.
- Folder – Much like an operating system folder, these exist within a bucket to enable organization.
Creating an Access Key
For NiFi to have permission to write to S3, we must set it up with an access key pair. There are many ways to do this, but the best practice is to create a new IAM user. To get to the IAM user screen, navigate to the IAM homepage.
-
Select “Add user” and check “Programmatic access”
-
Enter a new name such as “NiFi_demo”
-
Click “Next: Permissions”
-
Click “Create Group” and you will be presented with a list of permissions you can add to this new user
-
Enter a group name such as “Nifi_Demo_Group”
-
Next to filter policies search for S3 and check “AmazonS3FullAccess” > Click “Create Group”
-
At the bottom right, select “Next:Tags” > Click through to “Next:Review”
-
Click “Create user” to finish making an IAM User
The access key ID and secret access key are very important to setting up your data transfer. You can download them as a .CSV file or save them somewhere safe.
IMPORTANT: Be sure to record your secret access key as this is the only time it can be viewed.
Creating an S3 Bucket
Although we will cover the basics of creating your S3 bucket in this post, you can check out Cloud Academy’s Storage Fundamentals of AWS for an in-depth overview. Now that we have credentials for AWS, we need a place to land them. To put it simply, we need to create a new S3 bucket if you do not already have one. Go to the AWS S3 Console.
-
Click “+ Create Bucket”
-
Enter a unique bucket name and the region you are creating it in
-
Click through until the bucket is created (default options are fine to use)
-
Click on your new bucket and you should be able to see its contents — which will be empty
Setting up your NiFi & AWS Credential Service or Processor Controls
NiFi can be setup several ways including download from the Apache website or using a pre-made solution like Calculated System’s AWS Marketplace Offering.
NiFi has many ways to provide access to AWS either through an overarching credential service or parameters set to a specific processor. The credential service is ideal when you have multiple processors all relying on the same keys. For the scope of this tutorial, we will not be using the service, but it is ideal when moving into a production setting.
-
To get started, click and drag in a new processor “PutS3Object” > right-click “Configure the processor”
-
Under the Settings tab, you will see Automatically Terminate Relations > check the boxes next to “failure” and “success” since this is the last processor in the flow.
- Under the Properties tab, configure the following properties:
-
Access Key ID – From the User you created earlier and noted down
-
Secret Access Key ID – From the User you created earlier and noted down
-
Bucket – Put the name of the bucket you created
-
Region – The region your bucket is located; often U.S. East (N. Virginia)

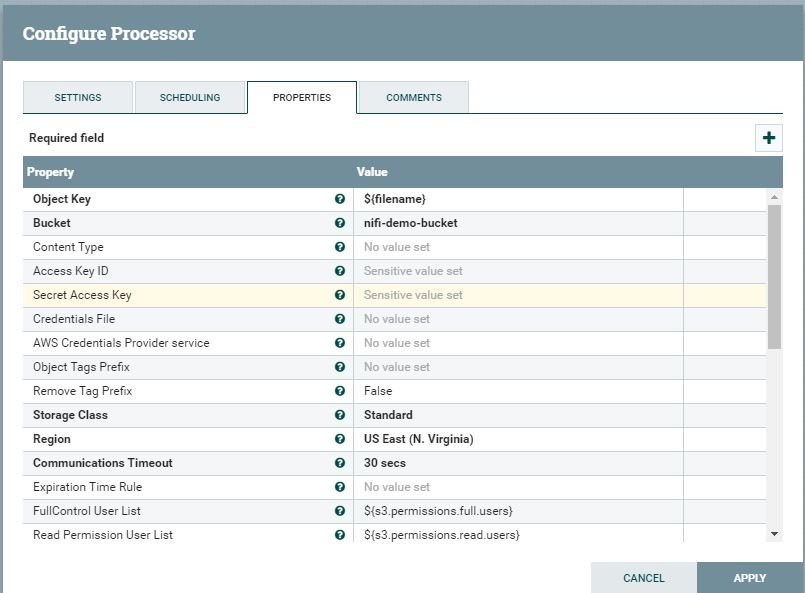
-
- Click “Apply” to finish up configuring the processor.
Setting Up Your Flow
For the purposes of this sample flow, let’s replicate NiFi’s own configuration directory to S3. To accomplish this, we need two additional processors: ListFiles and FetchFiles. Connect and configure them as shown below.


ListFile
-
Properties tab – Set “Input Directory” to /nifi/docs/html
-
Drag a connection from ListFile to FetchFile for relationship success
FetchFile
-
Settings tab – Check the boxes next to “Failure,” “not.found,” * “permission.denied”
-
Drag a connection from FetchFile to PutS3Object for relationship success
Running Your Flow
-
Right-click each of the processors > click “Start”
-
Let this run for a few seconds. If you want to track the progress, right-click into any blank space of your NiFi canvas and press “refresh.” You should see each processor reporting flowfiles “in” and “out”
-
For the purpose of this demo, right-click “Stop list files.” In production, you can leave this task running, but it is always best to stop demos when done. This stops the demo from producing sample files after you stopped using the program.
Viewing the Objects in S3
If you return to your bucket, you should see your files listed. Note: You may have to refresh button the page depending on your browser/settings.


[Optional] Security Cleanup
As an optional step, you may wish to revoke the access keys you gave to this Nifi Demo. It is general best practice to remove unused keys when done. To revoke the keys, go the AWS Console.
-
Click on the user you created earlier in the tutorial
-
Go to the Security Credentials tab and search for the Access Keys subsection. Here you can inactivate, delete, or even make new keys.
-
As a best practice, make the key inactive or delete the key.



