There are many use cases for tags, but what are the best practices for tagging AWS resources? In order for your organization to effectively manage resources (and your monthly AWS bill), you need to implement and adopt a thoughtful tagging strategy that makes sense for your business. The more quality information you have about your resources, the easier the management becomes.
As organizations put more workloads in the cloud, it’s easy to lose sight of the resources that you’re running. Spending, utilization, compliance, and security are all at risk if you don’t have a strategy to easily and quickly identify resources. Tagging helps ensure that all cloud resources are identifiable, easily discoverable, and available for reporting so that your organization gets the most value from your deployments.
In this post, we’ll discuss things to keep in mind when tagging your resources and how tags are important for your business.
What is a tag?
Tags are labels in the form of key-value pairs that may be attached to cloud resources such as instances, storage volumes, and databases. They provide additional information and context about that specific resource. Tags may identify who owns the resource, the environment where it is used, and any other technical or business attributes based on your requirements.
This example shows five tags of an EC2 instance that indicate business, technical, and security metadata relating to this particular instance.
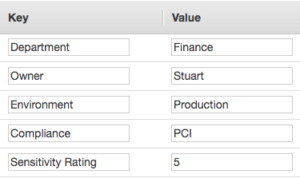

Before getting started with tags, it’s essential to establish a single standard that governs how tags will be managed by users across the organization. This should include the creation of a standard convention for naming resources that is easy to follow and that takes into account the policies of the different cloud providers you may be using. Amazon Web Services (AWS), for example, allows up to 50 tags per AWS resource, while Azure allows only 15. Each cloud provider has its own defined tagging guidelines and you’ll want to make sure that your tagging policy is consistent across platforms.
Design your tagging strategy
As cloud deployments grow, teams deal with an increasing amount of resources that are constantly moving, growing, and changing. Projects may be shared between teams or customers and can rely on different regions and platforms. This makes it easy to lose track of what’s being used until the bill comes due. For tags to be actionable at scale, most teams require visibility of exactly which resources are at play at any given time, who is using them, and what they are being used for, and who is responsible for them. Essentially, the more high quality information associated with a resource, the easier it becomes to manage.
Many organizations group tags into different categories. Examples of these categories include:
- Business
- Technical
- Security
Within each of these categories, you can then define your own tags that are specific to your organization for standardization. Some common tags include cost center, department, owner, environment, version, application, compliance, data sensitivity, and encryption.
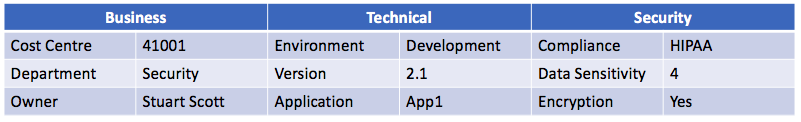

From a business perspective, we can clearly see who is responsible for the resource and its function within the business along with the cost center for financial reporting. From a technical perspective, we can see that the resource is currently in development and running version 2.1 of the App1 application. Our security tags indicate that this instance requires the data to be encrypted in order to comply with HIPAA compliance, and that we’ve set our internal data sensitivity rating at 4 on a scale from 1-5.
Too often, a resource is simply tagged with a “name.” The specific tags that you standardize across your organization will depend on your business and its structure. A thoughtful approach like the one provided above will give you far more actionable information about the resource down the road.
Best Practices for Tagging AWS Resources
Can’t wrangle your organization into a comprehensive tagging strategy, but want to cover the bases? Here’s what you should do at minimum:
1. Create cost allocation tags
The typical enterprise hosts resources across several cost centers (sales, marketing, finance, HR, etc.), projects, or teams (application developers, business analysts, service desk, training, etc.). Tags that identify or associate a resource with its specific business purpose and owner make it easier to accurately allocate spending.
Before you can use cost allocation tags, you must activate the feature from within the Billing and Cost Management Console:

Once activated, you can then select any of the tags you are using in your account to be included in reports using Cost Explorer. This will allow teams to generate a cost allocation report with the total monthly bill broken down by the enabled tags.
With costs accurately identified and allocated, teams can see which resources are incurring the greatest share of total cost, identify unused or duplicated resources, and identify potential opportunities to save money. In the AWS Billing and Cost Management console, the Cost Explorer tool can show spending by tags and deliver detailed billing reports.
Visit our course Cost Optimization Strategies for the Cloud for more information about how to optimize and reduce your cloud costs.
2. Create security and compliance tags
Security should be the priority for any deployment, so adding security-related tags to your resources should become a best practice for your organization.
Many workloads contain sensitive information or data that may be subject to auditing or reporting regulations such as GDPR or HIPPA. By tagging these resources appropriately, organizations can identify which resources require additional focus from a security standpoint.
As we saw in the example above, there was a tag called ‘Compliance’ with a value of ‘HIPAA.’ This easily helps you to identify which resources are being governed by which compliance certifications.
In addition to using tags to identify resources that are subject to a particular security or governance policy, tags can also be used to allow/deny access to resources by using conditions within IAM policies. For example
"Condition": {
"StringEquals": {"ec2:ResourceTag/Compliance": "HIPAA"}
This condition ensures that only resources tagged with a Compliance tag and a value of HIPAA are subject to the IAM policy. For more information on IAM policies and conditions, please see this AWS: Overview of AWS Identity & Access Management (IAM) course and our Hands-on Lab, Using S3 Bucket Policies and Conditions to Restrict Specific Permissions.
3. Leverage Resource Groups
Aptly named, Resource Groups are groups of resources bound together by their tags. Resource groups can be accessed and created either by using the AWS Systems Manager Console or by selecting ‘Resource Groups’ from the AWS Management Navigation bar at the top of the screen.
Resource Groups are used to help you manage your resources more effectively and to simplify the automation of tasks when the same task needs to be applied to a group of resources. For example, if you have a large number of EC2 instances all operating at the same layer of an application, you may decide to create a resource group for these instances. Doing so would allow you to implement a patch update to the group via a single task instead of scheduling multiple tasks, one by one.
The following image shows a new group being created that searches for all resources that have a tag of ‘Department’ with a value of ‘Finance’ in addition to a tag of ‘Environment’ and a value of ‘Production’.
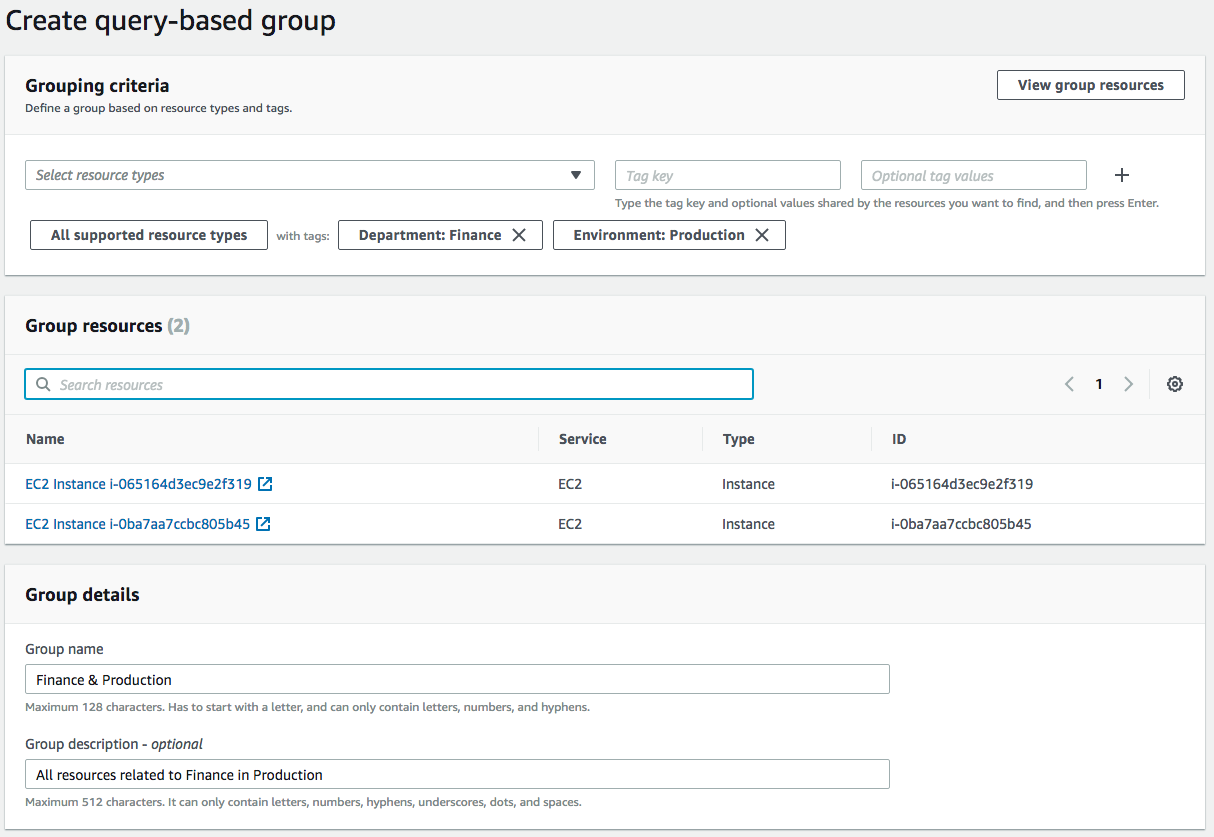

The interface allows me to easily group together all resources that are associated to Finance and that are currently in Production. Note that you can also filter by resource type, so I could have selected to filter this search purely on EC2 instances if needed.
Once a group is created, the group itself will be identifiable by its ARN which has the following syntax:
arn:aws:resource-groups:region:account:group/group-name
The region, account, and group-name will be yours.
4. Use Tag Editor
If you haven’t been tagging your resources as efficiently as you could have and you are now running hundreds or even thousands of resources in your environment, you might be thinking you have a daunting task ahead of you. However, the task becomes a lot easier when you use the Tag Editor.
Tag Editor allows you to search for existing resources based on Region, Resource Types, and existing Tags. Once you have found the resources that you want to apply additional tags to, you can add new Keys and Values in bulk.
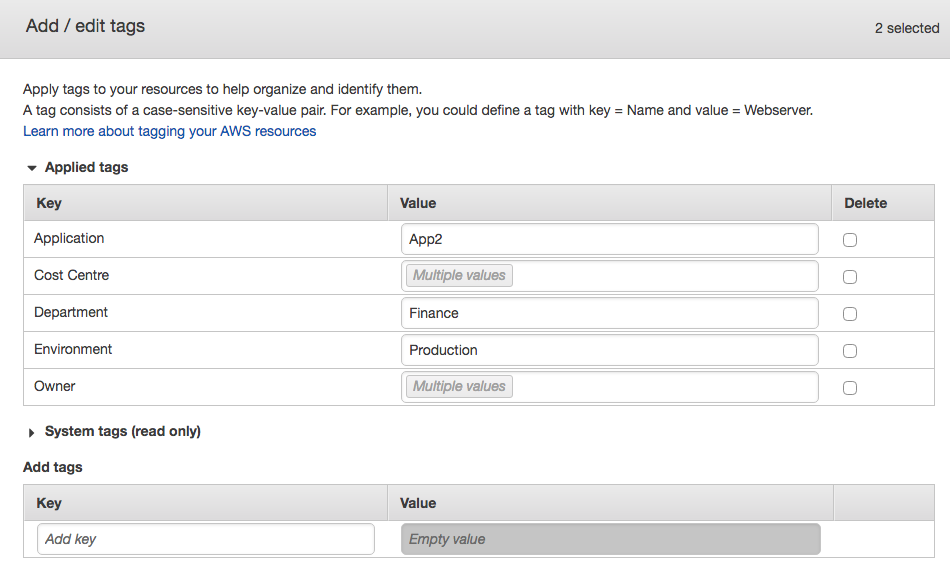

For example, if we add a new Key and Value in the fields in the interface as shown above, it will add the new tags to ALL the resources that matched our search criteria. The Tag Editor can be found by selecting Resource Groups from the AWS navigation bar and then selecting Tag Editor.
There are many use cases for resource tagging. This post has focused on some of the most common and important tactics in order to get a handle on your infrastructure. Standardizing a comprehensive tagging strategy does require some organizational discipline, but it pays off. It is highly recommended that you implement and adopt a tagging strategy that works for you to help manage your resources effectively and efficiently. The more reliable information that you have about your resources, the easier infrastructure management becomes.



