Learn how Aviatrix’s intelligent orchestration and control eliminates unwanted tradeoffs encountered when deploying Palo Alto Networks VM-Series Firewalls with AWS Transit Gateway.
Deploying any next generation firewall in a public cloud environment is challenging, not because of the firewall itself but because of the public cloud networking services that practitioners must use. The job of understanding and problem-solving around cloud networking complexities to ensure a successfully configured and maintained firewall deployment is no small task. It’s a task that is definitely possible — though difficult — and it comes with performance, scale, and visibility tradeoffs that need to be considered closely. This blog explores how to use Aviatrix’s intelligent orchestration and control service to simplify the deployment of Palo Alto Networks VM-Series Firewalls and eliminate those tradeoffs.
Aviatrix Firewall Network Service
Aviatrix’s Firewall Network Service is a service extension of its Enterprise Cloud Backbone Service. The Firewall Network service is a combination of Aviatrix services, combining both the intelligent controller and gateway services. The service enables simple insertion of Next Generation Firewalls (NGFW) into AWS Transit Gateway (TGW) environments, without sacrificing performance, scale, or visibility. The Aviatrix intelligent controller handles orchestration and dynamic updates for all routing elements within the AWS TGW environment, and the gateway service offers dynamic load balancing across multiple firewalls across high-performance links.
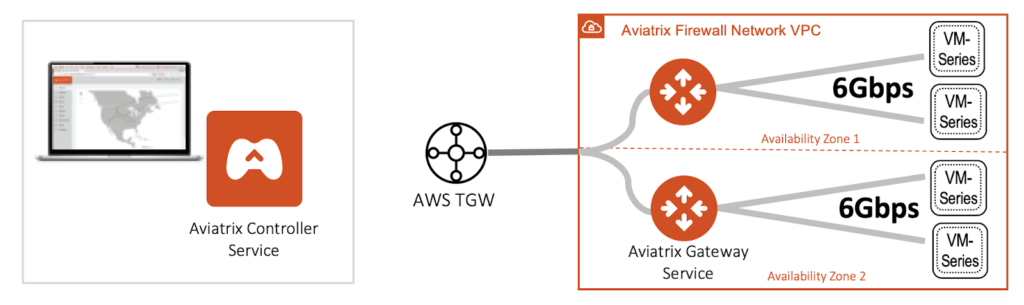

The Aviatrix Firewall Network Service leverages the combination of its intelligent orchestration and control as well as gateway services to remove AWS networking complexities such as lack of route propagation to VPCs, IPSec tunnels, and BGP; or use of source address translation (SNAT) between the firewall and the TGW. Eliminating these constraints allows Palo Alto VM-Series firewalls to operate at optimal performance and at TGW-native throughput. Removing the need to use SNAT allows session stickiness and source address to be retained for full visibility. The firewall network service is often deployed in multiple availability zones for active redundancy and scale-out load balancing. With Aviatrix, Palo Alto Networks VM-Series can achieve optimal performance, scale, and visibility.
Key benefits of bringing the Palo Alto Networks VM-Series to AWS TGW environments include:
- Easily Integrate NGFW into AWS Transit Gateway for threat detection and prevention.
- Eliminate IPSec bottleneck and leverage the best performance of the firewall.
- Enable scale-out and redundancy with ease.
- Automate end-to-end route propagation with Aviatrix intelligent orchestration and control service.
- Perform in-line traffic inspection based on user-defined policies.

Why You Need Aviatrix For Your Nextgen Firewall In TGW
Let’s discover further how Aviatrix helps secure your AWS Transit Gateway using next generation firewalls.
Get the best performance out of your firewall
Getting the optimal performance out of your NGFW in the cloud is all about feeding packets to the firewall in the most efficient manner. One of the most common ways of doing this today is to create IPSec tunnels between VPCs and the firewall instances. IPSec is an excellent technology for securing communications over the internet, but it inherently has performance limitations. An IPSec tunnel between the NGFW and VPC’s VPN Gateway (VGW) unnecessarily restricts bandwidth of the traffic going in and out of the firewall. No matter how much throughput the firewall can handle, IPSec will limit how much traffic a single instance of the firewall can process. This is like having a wide garden hose that’s clamped somewhere in the middle.
Ease the pain of firewall insertion in Transit Gateway
As stated earlier, in order to secure your AWS cloud with a next generation firewall using the resources and services that are provided by AWS, you will have to rely on VPN tunnels to pipe traffic to and from the firewall. This presents several challenges for the insertion of an NGFW. The first challenge is how to actually do this at scale. AWS Transit Gateway solves this issue to some degree but leaves a lot of room for improvement, such as the use case in which native VPC attachments require manual and static route management.
Automated route state management with Aviatrix
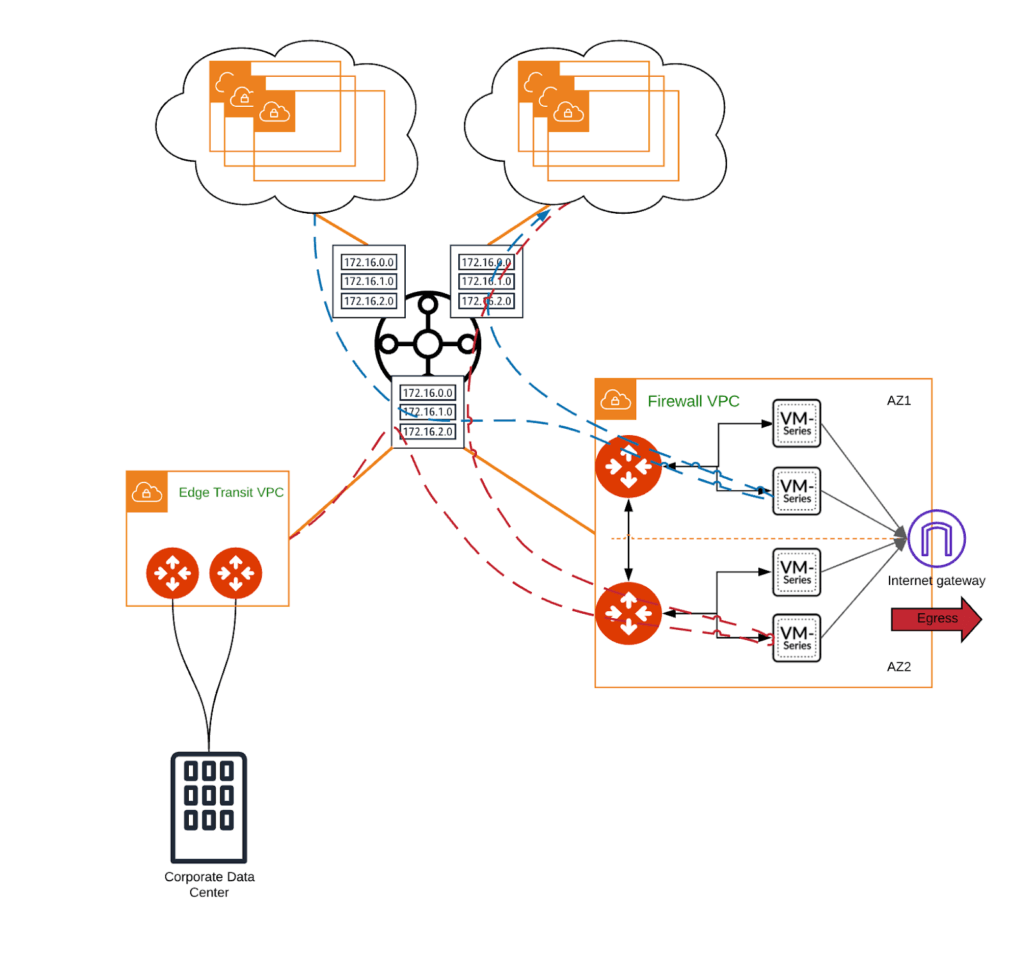
Aviatrix FireNet enables inspection of cloud traffic through a cluster of NGFWs, while maintaining native functionality and visibility. The Aviatrix controller handles orchestration and ongoing management of firewalls as well as critical elements of cloud networking, so that you don’t have to work around the limitations imposed by the cloud network controls. With Aviatrix, no manual modification of the route tables is required, as the controller handles propagation end-to-end.
Unleash the power of your firewall
In order to reach the highest level of optimization, you want every bit of your NGFW’s compute power to be spent on what it is meant to do: namely, threat detection, threat prevention, logging, etc. Aviatrix FireNet feature eliminates the need for IPSec and frees the NGFW from having to deal with any of the IPSec overhead.
Further, Aviatrix leverages native TGW attachments for forwarding traffic to firewall instances in the firewall VPC. This forwarding method offers very high throughput (50 Gbps) and low latency thanks to TGW VPC attachments, and does not introduce a performance bottleneck into your application’s design. This is a huge improvement over VPN tunnels connecting to VGW that cap at 1.25 Gbps. As such, it significantly improves the technical and economical efficiency of the entire architecture. In other words, you get more bang for your proverbial buck out of the firewall.
Scale without loss of visibility
As is the rule in the computing world, when you scale out you need to ensure that state is maintained properly across the scaled systems, and traffic is distributed accurately. Another major part of FireNet architecture is the use of Aviatrix gateways to do the load balancing across firewalls. If you have considered using AWS Transit Gateway and its Equal Cost MultiPathing (ECMP) capability, you may know that in order to avoid asymmetric routing, you need to perform source address translation at the firewall. This will replace the original source of the traffic with firewall’s IP, which could become problematic for any application that requires visibility into the traffic’s source address. For example, if we have an application that is tracking application transactions based on the source of the traffic, the source of the traffic will always be the firewall’s interface instead of the actual source. This diminishes the flexibility and applicability of this architecture for East-West inspection. With Aviatrix, you do not need to make this tradeoff between visibility and scalability. Aviatrix will manage load balancing across the firewall instances and retain visibility across all traffic.
Move fast with Aviatrix
Beyond firewall insertion, Aviatrix helps speed up build and management of your complex AWS environment. In our current cloud-based world, users have set high expectations for an infrastructure’s speed and agility. The complete Aviatrix Enterprise Cloud Backbone Service leverages a combination of intelligent orchestration and control with Aviatrix gateway technologies, in concert with native public cloud transit services to significantly increases IT agility in response to business requirement changes. Gone are the days of asking users to wait for weeks to get what they need in the cloud. Aviatrix decouples your operation from micro-configurations that are required to adapt to changes in the cloud. It orchestrates and automates the complex steps of building networks in the cloud, giving you the ultimate state that you are looking for. With that, you can react and service your business users and customers much faster.
To learn more, register for this upcoming webinar, “Best Practices for Deploying Palo Alto Networks VM-Series in an AWS Transit Network: Simplify Deployment and Optimize Performance, Scale and Visibility” taking place on May 23 at 10 am PT.





